What is a tor browser? You may have found out about the Tor program. It has been unmistakably included in reports throughout the years as an entryway to the entirety of the wrongs that hide in the piece of the Internet known as the dull web. Truth be told, notice of the Tor program is practically inseparable from getting to the dull web in certain circles.

The Internet that you can access by utilizing web indexes like Bing or Google is known as the surface web. The surface web involves just about 4% of the web’s substance. The remainder of the Internet consists of the profound web and the dim web. Data in the profound or dim web is just available through particular programs. The dull web is famous for facilitating locales that take part in a wide scope of criminal operations.
While you can utilize the Tor program to interface with locales in the profound or dull web, that isn’t the lone motivation to utilize the application. We will endeavor to disperse a few misinterpretations in regards to what Tor is and how it tends to be utilized. Here are the responses to seven inquiries you may have on the off chance that you are thinking about utilizing this program.
What is a Tor Browser used for?
It is an open-source internet browser that is allowed to download and utilize. It is accessible for Windows, Linux, Android, and you can even get a Tor program for your Mac. The word Tor represents the onion switch. The utilization of the onion representation will turn out to be more obvious as we investigate how Tor works.what is peak program
There is additionally a Tor network which is composed of many volunteer PCs which are generally running a particular worker application.
Is the program safe?
The Tor program can give a client secrecy while getting to the Internet just as permitting them to utilize exceptional administrations which are highlights of the Tor organization. Peak program packs in numerous dialects are accessible from the Tor download webpage.
What Problem is Tor Designed to Solve?
It is intended to thwart Internet checking known as traffic investigation. This checking strategy centers around the headers of the information bundles that make up messages sent over the Internet.
Regardless of whether you scramble the information bit of your information transmissions, data like source, objective, size, and different things can be dictated by contemplating the headers. Through an investigation of message headers it tends to be resolved which gatherings are speaking with one another and the size of the transmissions they are directing.
Disclosing this sort of data to any individual who may be observing the organization you are conveying on may not be however you would prefer. At times, it can present genuine monetary or actual peril by uncovering your personality to promoters or legislative organizations. Oppressive governments may bug people dependent on their online correspondence designs.
How Does Tor Work to Ensure Anonymity?
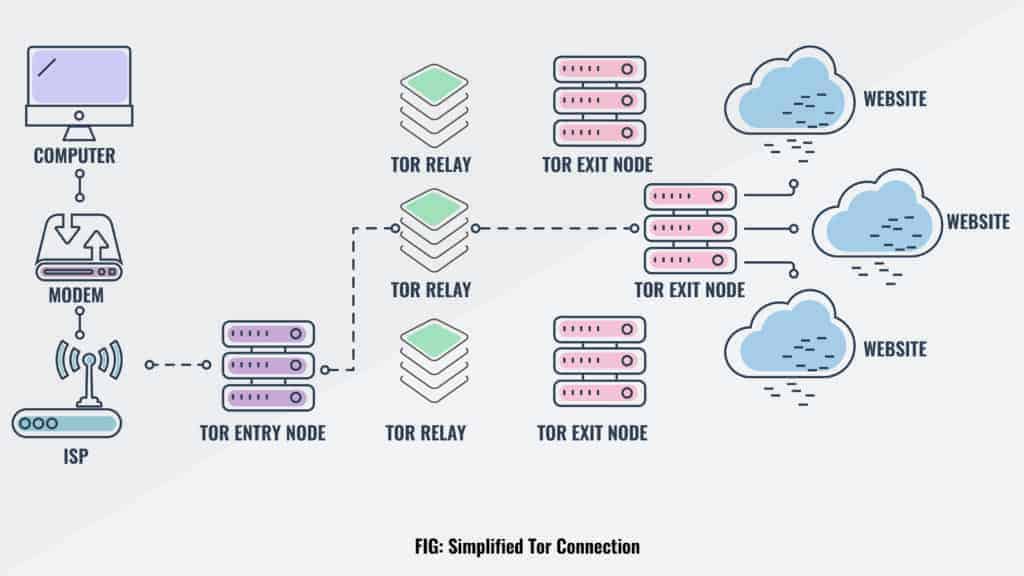
It makes an appropriated, unknown organization to safeguard the namelessness of its clients. Your web traffic is directed through the Tor organization (onion switch), viably anonymizing it. In straightforward terms, the Tor program associates with an openly recorded section hub, advances your information through haphazardly chose transfers, and afterward sends it out through an exit node.tor network
Jumping somewhat more profound, we track down that the private organization pathway is assembled gradually utilizing scrambled associations through network transfers. The way is broadened each bounce in turn, with a hand-off just realizing which transfer gave information and which hand-off will be the recipient. No transfer knows the total way. Thus, the obscurity of the sender is kept up.
How is Tor Used?
It is utilized for an assortment of reasons, not which are all legitimate. Some particular employments of Tor are:
Getting to .onion sites for what is onion browser, numerous associations, for example, the New York Times or Facebook have elective .onion destinations. You can’t utilize your normal program to associate with these destinations. Utilizing the Tor program permits you to get to these destinations secretly, maybe undercutting government oversight.
It can be utilized as an option in contrast to a VPN when keeping your perusing history private is wanted. It will keep your online developments hidden without the need to introduce an extra programming bundle.